Reclaim Your Privacy and Peace With These 11 Smart Ways
Online privacy is no longer just a tech concern. It affects how your data moves, who profits from it, and what assumptions get made about you without your knowledge. Most platforms collect far more than needed. Taking back control doesn’t require huge changes—it just takes smarter choices.
Here are some approaches that show how to limit exposure, block tracking systems, and make your online behavior harder to profile, while keeping your experience simple, secure, and reliable.
Switch Browsers That Don’t Feed Ad Networks

Credit: iStockphoto
Brave, Firefox, and Opera don’t send your data to the same large-scale ad platforms that Google Chrome does. These browsers block most third-party trackers and fingerprinting scripts right away. You won’t need extra extensions just to protect basic activity. When fewer tracking tools run in the background, pages load faster and ads become less targeted.
Use DuckDuckGo Instead of Google Search

Credit: flickr
Google collects search behavior and combines it with your browsing history, device location, and account activity. That’s how it delivers hyper-personalized results—and why ads feel unusually relevant. DuckDuckGo, on the other hand, doesn’t track your history or store personal data. Its search results remain the same for everyone using specific keywords.
Opt for Automatic Updates for Devices and Apps
Credit: Canva
Attackers use security flaws that developers have already fixed—but only if users install those updates. Once a vulnerability becomes known, it’s quickly added to the list of tools hackers rely on. Delaying updates keeps those flaws open longer than necessary. Devices that stay unpatched become easy entry points, especially on public networks or shared machines.
Adopt a Password Manager for Safer Logins

Credit: Getty Images
According to a 2022 Verizon report, over 80 percent of hacking breaches involve stolen or reused credentials. Password managers reduce that risk by generating strong, unique passwords for every site. They store those passwords securely and autofill login fields when needed. You only have to remember one master password.
Check That Sites Use HTTPS Before Sharing Data

Credit: Getty Images
If a site doesn’t use HTTPS, your activity on that page can be visible to others on the shared network. That’s especially risky when entering personal or financial information. HTTPS protects the connection and adds a layer of protection between you and the server. Look for a lock symbol next to the website’s address.
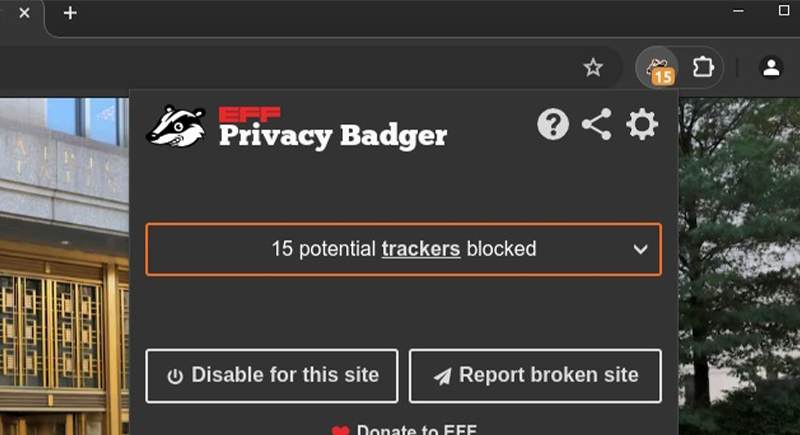
Install Tracker Blockers, Not Just Ad Blockers
Credit: Instagram
Blocking ads helps declutter your screen, but doesn’t always stop trackers that collect behavioral data. Extensions like Privacy Badger and uBlock Origin go further by prioritizing the actual scripts that gather information across websites. And the best part is that such trackers are usually invisible and embedded in social buttons, videos, and analytics tools.
Use a VPN That Encrypts All Traffic

Credit: pixabay
Without a VPN, your internet provider can see every site you visit, even if the content is encrypted. Advertisers use your IP address to estimate location, link browsing across devices, and serve targeted ads. Public networks expose even more and make it easier for others to intercept unprotected traffic.
Limit App Permissions to Only What’s Needed

Credit: iStockphoto
Many apps ask for full access to location, camera, contacts, or microphone, even when they don’t need it. These permissions usually stay active in the background. Over time, that creates an ongoing stream of data collection. Go through your app settings and turn off access that doesn’t align with what the app actually does.
Use Signal for Private and Secure Messaging

Credit: pexels
Signal uses end-to-end coding by default, which means only the people in the conversation can read the messages. The app doesn’t store metadata, such as who contacted whom or when. You also don’t need a separate account or email address, and can use this like a standard messaging app.
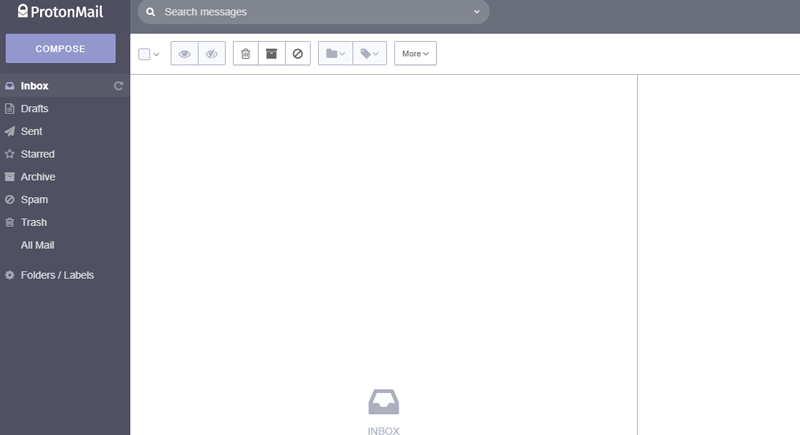
Switch To Email Services That Don’t Scan Messages
Credit: Wikimedia Commons
Free email providers often scan your inbox to shape advertising profiles. They use content and subject lines to predict interests and suggest ads. Services like ProtonMail and Fastmail avoid this entirely. They don’t serve ads or sell user data. ProtonMail even stores messages encoded at rest and only decrypts them on your device.
Audit Accounts and Data Every Three Months

Credit: Wikimedia Commons
Every few months, check your most-used services for signs of exposure. Visit HaveIBeenPwned.com to see if your accounts were involved in data breaches. Review saved devices and connected apps under your account settings. Remove old logins, update weak passwords, and turn off unnecessary connections.
Avoid Using Google or Facebook to Log In
Credit: iStockphoto
Social logins seem convenient, but they link your behavior across dozens of services. When you use one account to access others, data gets shared between platforms even when you’re not active. In case you delete the original account, access to those connected services can be broken.
Add Two-Factor Authentication to Key Accounts

Credit: Getty Images
Skipping two-factor authentication means your entire account depends on just one password. If that password gets leaked, guessed, or reused across services, attackers can log in without resistance. Once inside, they can change recovery settings, lock you out, or access sensitive information.
Uninstall Apps You Rarely Open or Trust

Credit: iStockphoto
Old or rarely used apps tend to get ignored, but they still run background services or request access to your device’s features. Developers may abandon the app, stop patching bugs, or sell the user base to less reputable companies. Doing a routine audit helps you identify apps that no longer serve a clear purpose.
Create Email Aliases for Different Services

Credit: iStockphoto
Aliasing tools let you generate unique email addresses that all forward to your main inbox. This separates your accounts and gives you a better idea of which services sell or leak your information. Using aliases also reduces the risk of a single breach giving attackers access to everything tied to one account.