19 Daily Habits That Unknowingly Put Your Privacy at Risk
Crafting an article that taps into the pulse of our privacy concerns with a blend of wit and wisdom, here we go. This piece is your ticket to understanding the little things we do daily that might as well be invitations to privacy invaders. So, buckle up!
The Unseen Eyes in Your Inbox
Credit: flickr
Opening emails without a second thought? We’ve all been there. But clicking on links from unknown senders is like leaving your house keys in the door. Scammers can use these to install malware and spy on your information. Next time, if you don’t know where it’s from, let it stay unclicked.
Social Media Overshare Fiesta

Credit: flickr
Who doesn’t love sharing their life’s highlights? But oversharing on social media is like giving a bullhorn to your personal details. From your pet’s name to your favorite pizza topping, these tidbits are gold for hackers guessing your passwords. Maybe think twice before you share your next “10-year challenge.”
Public Wi-Fi: The Hacker’s Playground

Credit: Wikimedia Commons
Logging into free Wi-Fi at your favorite coffee shop might seem harmless, but it’s a prime spot for eavesdroppers to snatch your data. Using public Wi-Fi without a VPN is akin to shouting your secrets across a crowded room. So, keep those tasks for a secure connection back home.
The Perils of ‘Remember Me’
Credit: Wikimedia Commons
Convenience at the click of a button, right? Wrong. Using the ‘Remember Me’ feature for online accounts is like leaving your diary open on the kitchen table. Anyone with access to your device can take a peek. Always log out, especially on shared devices.
Ignoring Software Updates is a Risky Game
Credit: flickr
Postponing software updates is like ignoring a leaky faucet; it only worsens. These updates often contain vital security patches that protect your data from new threats. By delaying, you’re giving hackers a head start. Make updating a priority.
The Location Tracker You Didn’t Know You Had
Credit: pexels
Ever checked in to a place on social media or shared a live location? Congratulations, you’ve just handed out a map of your movements. This info is a treasure trove for stalkers. Keep your whereabouts off the digital grid.
The App Hoarder’s Dilemma

Credit: pexels
Downloading apps for everything under the sun? Each one is a potential leaky vessel for your personal data. Be selective about the apps you install and regularly review permissions. Your phone’s storage will thank you, too.
Password Fatigue Syndrome
Credit: Wikimedia Commons
Using the same password for multiple accounts is like having one key for everything you own. Once a hacker gets it, they can access your entire digital life. Invest time in unique passwords for each account. It’s a hassle, but so is identity theft.
The Secret Spy in Your Pocket

Credit: pexels
Your smartphone can become a mini spy device if you’re not careful. Apps with microphone and camera permissions can listen in and watch, even when you think they’re off. Regularly check which apps have these permissions and revoke them if they don’t need them.
Clickbait: The Temptation Trap
Credit: flickr
We’ve all clicked on headlines that seemed too juicy to resist. But these headlines are often lures for phishing sites designed to steal your info. If it sounds too sensational, it probably is. Stay skeptical, friends.
The Dangers of Digital Eavesdropping

Credit: Wikimedia Commons
Smart speakers and virtual assistants are super handy, but they’re also listening—always. They can pick up more than just your commands, including conversations. Think about what you say when they’re listening.
The Endless Email Trail

Credit: flickr
Sending sensitive info via email is like leaving a breadcrumb trail for hackers. Encrypt sensitive emails or use secure sharing platforms. Your personal information should be as secure as Fort Knox.
Thrift Shopping Your Tech

Credit: Wikimedia Commons
Buying used smart devices can save a few bucks, but you might also inherit the previous owner’s data or malware. Always reset the used tech to factory settings before you start using it.
The Autocomplete Trap
Credit: flickr
Autofill is a convenience feature that can backfire in a snap. It stores your personal and payment info, which phishing websites can harvest. Type it out manually to stay safe.
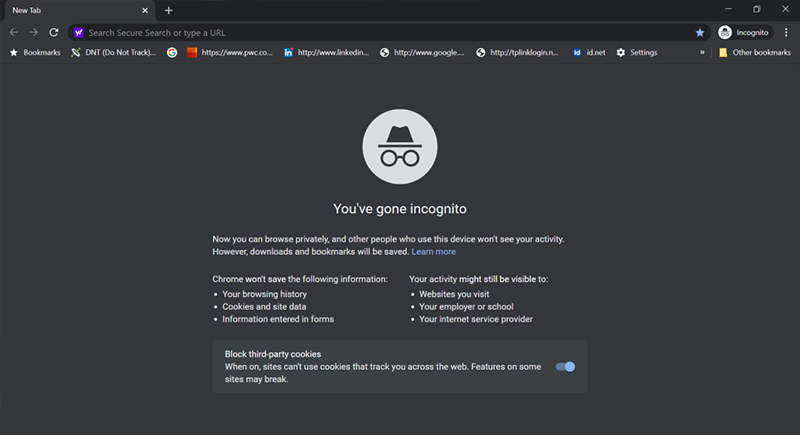
The False Security of Incognito Mode
Credit: Wikimedia Commons
Browsing in incognito mode doesn’t make you invisible online. Your ISP and websites can still track your activity. For absolute privacy, consider using a VPN along with incognito mode.
The USB Stick Lottery

Credit: flickr
Plugging in a found USB stick is digital Russian roulette. It could be loaded with malware waiting to infect your device. Curiosity killed the computer—avoid the temptation.
Not Securing Your Wi-Fi Fortress

Credit: Wikimedia Commons
An unsecured home Wi-Fi network is like an open door to your digital home. Secure it with a strong password and WPA2 encryption. Don’t make it easy for digital trespassers.
The Ghosts of Online Accounts Past

Credit: flickr
Old, unused online accounts are like digital ghosts—they can come back to haunt you, making them easy targets for hackers. Close accounts you’re not using to seal off potential entry points.
The Trap of Free Trials
Credit: flickr
Signing up for free trials without reading the fine print can lead to unwanted subscriptions and your payment info being stored where you might not want it. Always keep track of your trials and cancel them before they auto-renew.